Most vulnerable OSes and applications in 2014
By Cristian Florian, GFI LanGuard Product Manager, GFI Software
Friday, 27 February, 2015
An average of 19 vulnerabilities per day were reported in 2014, according to the data from the US National Vulnerability Database (NVD). The NVD provides a comprehensive list of software security vulnerabilities. In this article, I look at some of the trends and key findings for 2014 based on the NVD’s database.
Some of the questions asked are:
- What are the latest vulnerability trends? Are we seeing an increase or a decrease in the number of vulnerabilities?
- What percentage of these vulnerabilities are rated as critical? (For example, high-security impact - like allowing remote code execution - and thus easy to exploit.)
- In which areas do we see the most vulnerabilities? Are operating systems, third-party applications or network devices such as routers, switches, access points or printers most at risk?
- Which operating systems and applications are listed with most vulnerabilities? This data is important because the products which are on top get the most frequent security updates. To maintain an IT infrastructure secure, sysadmins need to continually monitor these operating systems and applications for the latest updates and ensure they are always fully patched.
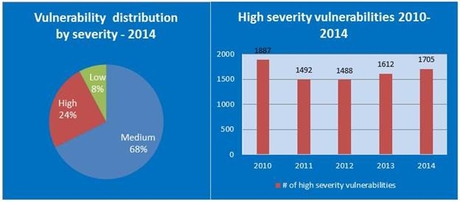
7038 new security vulnerabilities were added to the NVD database in 2014. This means an average of 19 new vulnerabilities per day. The number is significantly higher than in 2013 and continues the ascending trend over the past few years.

24% of these vulnerabilities are rated as high severity. The percentage is lower than in 2013, but the actual number of high-security vulnerabilities has increased compared to last year.

Third-party applications are the most important source of vulnerabilities with over 80% of the reported vulnerabilities in third-party applications. Operating systems are only responsible for 13% of vulnerabilities and hardware devices for 4%.


It is interesting that although Microsoft operating systems still have a considerable number of vulnerabilities, they are no longer in the top 3. Apple with OS X and iOS is at the top, followed by Linux kernel.
2014 was a tough year for Linux users from a security point of view, coupled with the fact that some of the most important security issues of the year were reported for applications that usually run on Linux systems. Heartbleed, for example, is a critical security vulnerability detected in OpenSSL while Shellshock is a vulnerability that affects GNU Bash.

The applications listed here are pretty much the same as in 2013. Not surprisingly at all, web browsers continue to have the most security vulnerabilities because they are a popular gateway to access a server and to spread malware on the clients. Adobe free products and Java are the main challengers but web browsers have continuously topped the table for the last six years. Mozilla Firefox had the most vulnerabilities reported in 2009 and 2012; Google Chrome in 2010 and 2011; Internet Explorer was at the top for the last two years.
To keep systems secure, it is critical that they are fully patched. IT admins should focus on (patch them first):
- Operating systems (Windows, Linux, OS X)
- Web browsers
- Java
- Adobe free products (Flash Player, Reader, Shockwave Player, AIR)
To conclude, the aim of the article is not to blame anyone - Apple or Linux or Microsoft. The message I am trying to get across is that all software products have vulnerabilities. The frequency of security updates increases with the product’s popularity.
At GFI we would like the people to use the information as a guide and to show which areas to pay more attention to when patching their systems. At the end of the day, however, an IT admin’s attention should be on ALL products in his network and not limited to those at the top of the vulnerability list; neither should the assumption be made that those further down the list are safer. Every software product can be exploited at some point. Patching is the answer and that is the key message.
Why we need to redefine cybersecurity success to support CISOs
When Notifiable Data Breaches statistics are released we should look at the nature of the...
Is 2026 the year of identity? Just follow the money
What $40 billion in cyber acquisitions says about the future of identity security.
Proactive cybersecurity must lead innovation in Australia’s AI future
AI presents extraordinary opportunities for productivity, innovation and growth but it also...




