Protecting yourself against CryptoLocker
By David Higgins, ANZ Country Manager, WatchGuard Technologies
Wednesday, 02 September, 2015
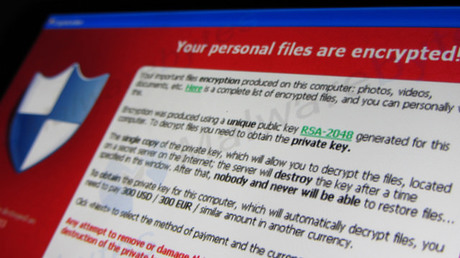
One of the biggest crises in security over the past 18 months has been CryptoLocker, the ransomware Trojan that encrypts files on shared and mapped drives before demanding payment for the decryption key.
First observed almost a year earlier, the initial version of the malware was isolated in mid-2014. Since then, new variants have appeared including a version that specifically targets Australian organisations. The original version encrypted Office documents and PDFs whereas newer variants are casting a much wider net that is affecting critical business data such as database, payroll and accounting files. Most versions of Windows are vulnerable to attack, but as at the time of writing, no Apple versions have been recorded.
To restore access to their files, users are required to pay a set ransom by credit card or Bitcoin. With ransom demands currently ranging anywhere between US$600 to US$3000, it’s clear a successful CryptoLocker attack can be a major IT headache. These attacks can often result in hours, days or even indefinite loss of access to data.
The threat
Usually the Trojan arrives as an .exe attachment to an email. It can also gain entry if the email recipient clicks on an embedded link that leads to a malicious website where the .exe file automatically begins to download.
Slightly less frequently, the Trojan is delivered when visiting a legitimate website that has been unknowingly compromised by an SQL injection. (A number of infections in 2014 are believed to have been caused courtesy of a federal government department’s compromised website.)
Originating in Russia, the Australian variant of CryptoLocker sports branding and identification vaguely similar to Australia Post but falls down in its use of English as the email contains numerous grammatical and spelling errors.
What happens
If the recipient fails to notice the mistakes and clicks on the link, they are taken to a site sporting the Australia Post logo and are invited to download information about a parcel. The executable CryptoLocker file is then installed. After that, it may take a few minutes or even an hour or two before the following message appears on their screen:
“Your files including those on the network disk(s) are now encrypted with the CryptoLocker virus”
To regain access to the files, the recipient must click on yet another link, which takes them to a site where the ransom can be paid. The ransom demand is likely to come with a time limit, after which decryption will no longer be an option. The preferred currency for this is Bitcoin. Some variants of ransomware have taken customer service to a new level with live chat support available to guide users through the payment process. Ransoms have also been increased after set time limits to motivate users to pay quickly, often handing over their credit card details and unknowingly installing software to record keystrokes during the process through a malware infected landing page.
Staying protected
The best way to avoid CryptoLocker is to educate yourself on best practices and establish multiple layers of security. These layers could exist on a single device such as a firewall or managed separately. Adding a healthy dose of scepticism to your online activities can also save you in the long run.
Layer 1: Stop spam emails. To stop the arrival of emails containing CryptoLocker, make sure you have effective spam protection and effective policies. A prerequisite is attachment control to ensure all .exe files delivered by email are disabled. Given the emails include links to malicious sites, use DNS and URL block lists. Finally, check your cloud email security.
Layer 2: Protect against exploits. Software vulnerabilities allow hackers to take advantage of your system and can lead to your website becoming a host for malware. To avoid vulnerabilities, keep your systems and software up to date by updating and installing patches regularly and consistently.
Layer 3: Prevent malicious links from doing damage. Use URL filtering to prevent access to malicious websites. Because of the rapid rate of evolution of threats such as CryptoLocker, the solution should be one that is updated constantly. Look for a filter that uses reputation enabled defence, where the filtering solution continually gathers and shares security feedback from other devices, filtering engines and users.
Layer 4: Detect and stop the CryptoLocker package. For advanced systems and greater protection, consider using a system to block advanced persistent threats. Our APT Blocker can identify malicious files based on their activity rather than relying on major antivirus vendors to update their systems after a new variation has already infected other systems. This zero-day protection can scan files and identify exactly what it is they’re trying to do on your system and block it before it can be activated.
Layer 5: Detect and prevent CryptoLocker actions. If you can prevent CryptoLocker from communicating with its command and control servers, or from accessing strange ports, you can stop the malware from creating the encryption key and prevent it from encrypting your files.
This requires a firewall policy that controls outbound and inbound traffic by only allowing activity over required ports. Use proxies where possible and use application control to whitelist other ports (eg, NTP/123). Other sensible strategies include: require authentication to use the internet, use SSL inspection and establish a policy of providing users with the least amount of user access. Also, don’t forget to back up mapped drives when not in use because if CryptoLocker makes it into your organisation, it will hijack these drives along with everything else.
Layer 6: Log, report and monitor web traffic. Most organisations have some kind of software in their firewall or unified threat management solution that logs web traffic, but it’s important you don’t simply generate reports. Review them regularly to understand what is occurring on your network and to see if an attack has been foiled.
Layer 7: Recovery. If all else fails and you are attacked, there are only two options. Pay the ransom or restore from backups — providing the backups are still intact. For this reason, it’s a good idea to carry out additional daily backups on devices that aren’t mapped, such as USB drives.
Layer 8: User awareness. This is one of the simplest steps you can take but it can also be the most difficult. Train your users to be suspicious of every attachment on every link in an email. Teach them to identify poor grammar and spelling errors as a sign of potential malicious intent in emails and websites, and ask them to report suspicious activity to IT.
By exercising caution, improving user education and maintaining best practices, you can avoid being hit by CryptoLocker. The best method of protection against this attack is still deploying an advanced persistent threat solution to detect and block these attacks before they end up costing you in time, finances, data and recovery.
Why we need to redefine cybersecurity success to support CISOs
When Notifiable Data Breaches statistics are released we should look at the nature of the...
Is 2026 the year of identity? Just follow the money
What $40 billion in cyber acquisitions says about the future of identity security.
Proactive cybersecurity must lead innovation in Australia’s AI future
AI presents extraordinary opportunities for productivity, innovation and growth but it also...



