TorrentLocker spoofing AusPost, AFP to fool victims
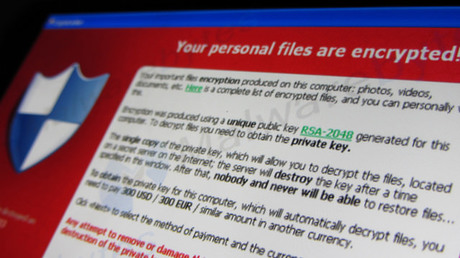
Spoof websites masquerading as legitimate pages from organisations including Australia Post, the Australian Federal Police and New Zealand Post are being used in a ransomware campaign targeting local internet users.
The TorrentLocker campaign uses targeted spam to lure potential victims and provides highly localised download, ransom and payment pages, research from ESET shows.
Spam messages link to a localised web page claiming a document must be downloaded. The email campaigns using major Australian and New Zealand organisations were identified between April and August, ESET said.
Other recent campaigns have targeted countries in Europe, including the UK, Austria, Spain, Italy, Sweden, Poland, Turkey and the Netherlands. Distributed URLs are only accessible using IP addresses that appear to originate from the country targeted by the individual campaign.
TorrentLocker has remained active since ESET first analysed the ransomware family in 2014 but has been modified in recent variants to circumvent mechanisms protecting internet users in targeted countries.
Recent additions include modifying the way TorrentLocker contacts its command and control servers, protection of these servers with a new layer of encryption and the process of encrypting users’ files.
“These newer TorrentLocker variants have really upped the ante,” commented ESET Senior Research Fellow Nick FitzGerald.
“Earlier variants, just like other crypto-ransomware, encrypted files of specific types, as determined by their filename extension. The recent variants turn that approach on its head, encrypting all files except for a few types necessary to allow the system to keep working after the file system has been encrypted.”
These changes have modified the kinds of backups that need to be kept to fully restore a system encrypted by the ransomware.
ESET is urging Australian victims of ransomware attacks not to pay the ransom, as there is no guarantee that files will be properly decrypted.
“Ransomware is very active in Australia and New Zealand and will be increasingly targeting users moving forward,” FitzGerald said.
“Users shouldn’t panic when encountering these kinds of situations and follow best practices to retrieve their data. Proactive prevention and protection can significantly reduce the risks and impact of malware and ransomware attacks.”
Akamai and Visa collaborating to secure agentic commerce
Akamai and Visa have formed a strategic partnership aimed at providing security solutions for the...
Kyndryl unveils quantum safe assessment service
Technology services company Kyndryl's quantum safe assessment service aims to help...
Australian orgs the most targeted by ransomware in 2025
Australian organisations were the most targeted by ransomware among organisations in 10 markets...



